Intro to Malware
Types of malware
- Target
- Mass
- Specific
- Forms
- Trojan Horse: Beware of Greeks...
- Virus: Spreading by host file
- Worm: Spreading by vulnerability
Information Stealing
- Collect information from computer and send it to the attacker
- Keyloggers: Actively recording everything typed
- Sniffers: Monitor for anything that looks interested
- Password stealers: Grab autocomplete and password information from web browsers and send them off
- Intercepting: Browser extensions, proxy or similar technologies to intercept and manipulate web traffic
Remote Access
- Backdoor
- Allows an attacker remote access
- Commonly a remote shell
- Botnet
- P2P networks, IRC, Twitter...
- Listen and wait for commands
Ransomware
- Silently install, and start encrypting files in the background that you’re not using
- using asymmetric encryption, so you’d never have had the key on the system
Rootkit
- Hooking into operating system calls and changing their behaviour
- Conceal the payload
- If you can’t see it, you can’t easily remove it
- Common examples
- File and directory hiding
- Process hiding
- Registry hiding
- Falsified files
- Preventing applications from running
- Resisting removal
Downloaders and Launchers
- Specific standalone code to bundle other malware
- Downloaders/Droppers
- Launchers
- To launch other malware
- Generally to make use of exploits and launch in a specific way
Malware on Windows
- Portable Execute format (PE)
- Linking
- Static: Code from library is in executable
- Dynamic: Imports listed, OS loads at start
- Runtime: Connect to libraries only when function needed
- PE Header
- Information about the entire file
- Type of code
- Flags (e.g. executable, DLL)
- Linking information
- Size and memory information
PE Sections
- PE file made up of sections
- Sections have names, flags (e.g. executable) and content
- Typical layout:
- .text
- Instructions–whattheCPUexecutes
- Containstheexecutablecode
- .rdata
- Imports and exports
- .data
- Globaldatafortheprogram
- .rsrc
- Resources used by the program (e.g. icons, dialogs, strings)
- .text
PE Execution
- Extract entry point, heap and stack sizes from PE header
- Iterate through sections and load into virtual memory
- Find address of entry point from symbol table
- Load imports
- Create a new thread at that address, and execute
Linking Information
- Imports
- What will be called outside
- DLLs – libraries of functions that you can use
- get used to seeing certain DLLs
- Kernel32.dll – Core functionality (memory, files, hardware)
- Advapi32.dll – Windows components (service manger, registry)
- User32.dll - User interface components
- Gdi32.dll – Display
- Ntdll.dll – Interface to windows kernel
- WSock32.dll/WS2_32.dll – Winsock (network)
- Wininet.dll – High level networking functions
- Exports
- What can be called inside
- Dllmain
- What can be called inside
Common techniques employed
Persistence
-
Malware generally needs to persist between system boots
-
How can they make sure they load each time?
- Logon (Shell, Run)
- Explorer hooks
- Scheduled tasks
- Services
- Drivers
- Boot execute
- AppInit (DLL loaded into every application that starts)
-
Generally: Remove their persistence, remove the malware!
-
If the malware is running
- Make it hard to stop the Malware once it is running
- Prevent removing/changing the persistence
- Hide the presence of persistence (Rootkit behaviour)
-
RunOnce
- Every boot, the malware is loaded from the RunOnce key, then removed – but it’s in memory
- No tools will show it as being persistent anywhere, as the RunOnce key is no longer populated
- On a clean shutdown, write back to the RunOnce key
- Solution: Don’t clean shutdown!
Stealth
- Camouflage against legitimate system files
- Pretend to be Microsoft
- Inject into other processes
- Replace legitimate files
- Hiding from the operating system
- Rootkit time
Analysing Malware
Basic Static Analysis
- Examine the PE file itself
- Signature: What was it compiled with?
- Structure: Is it packed?
- Sections: How is the file made up?
- Metadata: What other information is there?
- Certification: Has the file been digitally signed?
- Imports: What does it use?
- Exports: What does it make available?
- Strings: What text does it contain?
- Resources: What icons, menus, dialogs does it have?
Signature & Structure
Detect it Easy
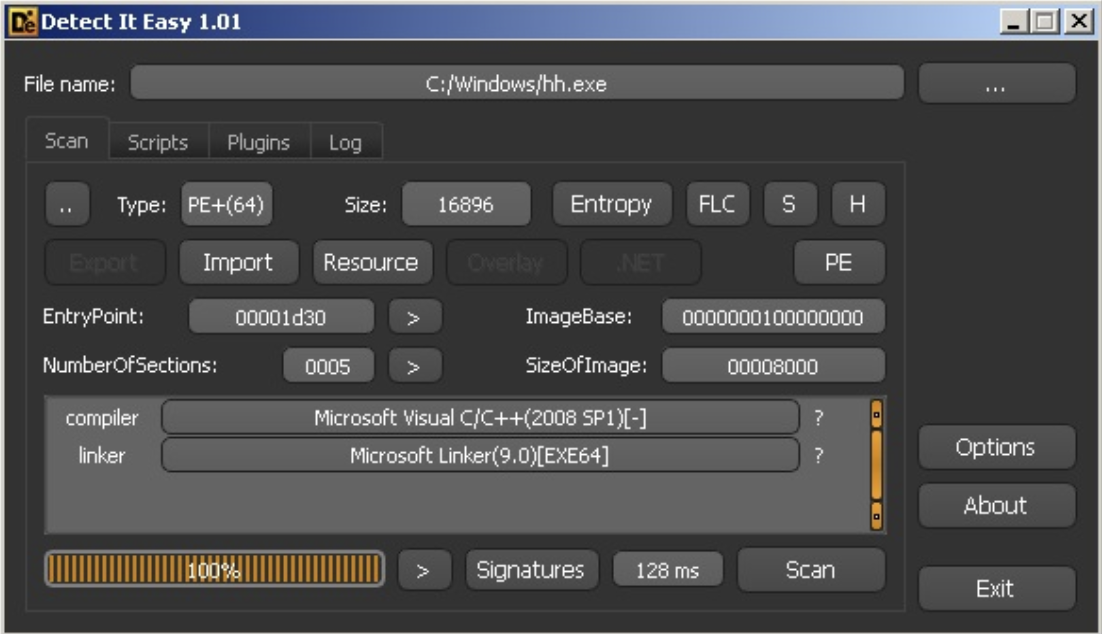
- Helps you before you try to do static analysis
- Uses signatures for PE information
Examining the PE File
- The Portable Executable (PE) file format is used by Windows executables, object code, and DLLs
- The PE file format is a data structure that contains the information necessary for the Windows OS loader to manage the wrapped executable code
- The information in the PE can provide valuable information to the malware analyst
- Use DependencyWalker and Peview to examine a PE file
PE File Structure
Header
- stores information about every library that will be loaded and every function that will be used by the program
Sections
- .text Contains the executable code
- .rdata Holds read-only data that is globally accessible within the program
- .data Stores global data accessed throughout the program
- .rsrc Stores resources needed by the executable
Packing and Obfuscation
-
Is it packed?
- Barely any imports
- No useful strings
- Non-standard names of sections o Section specifications
- Section contains code
- Section can be executed as code o Size differences
- Two main functions
- LoadLibrary
- GetProcAddress
- Other functions
- Functions which work with virtual memory
- Functions to work with libraries
-
Is it obfuscated?
- No useful names
- Conventions not adhered to
- No useful strings
Sections and Metadata
PEStudio
Imports and Exports:
Dependency Walker
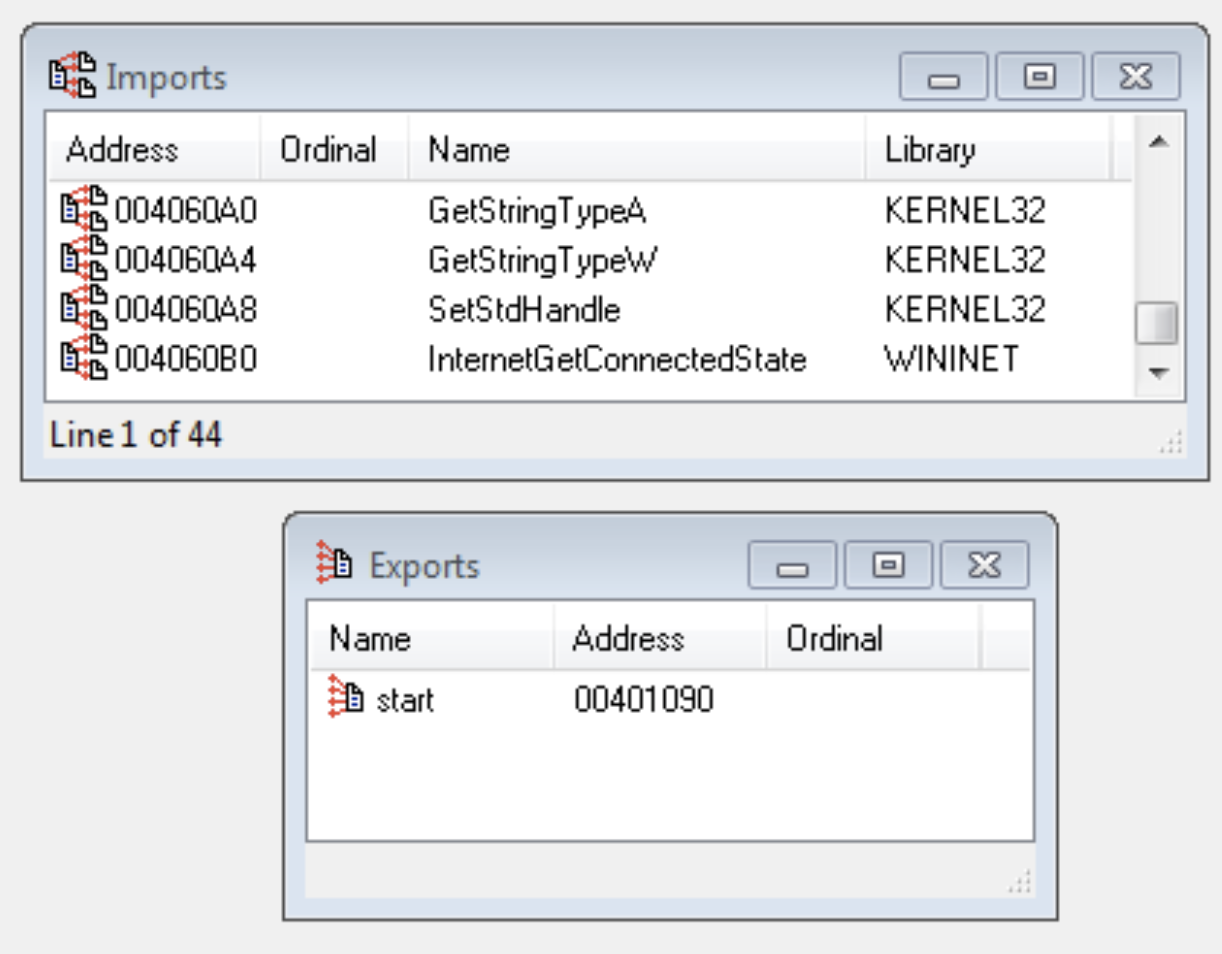
- Imports: What functions does the malware use
- Only includes those directly accessed
- Exports: What functions does the malware make available – when the malware isn’t a single file
- Dependency walker breaks this down for us
Common DLLs
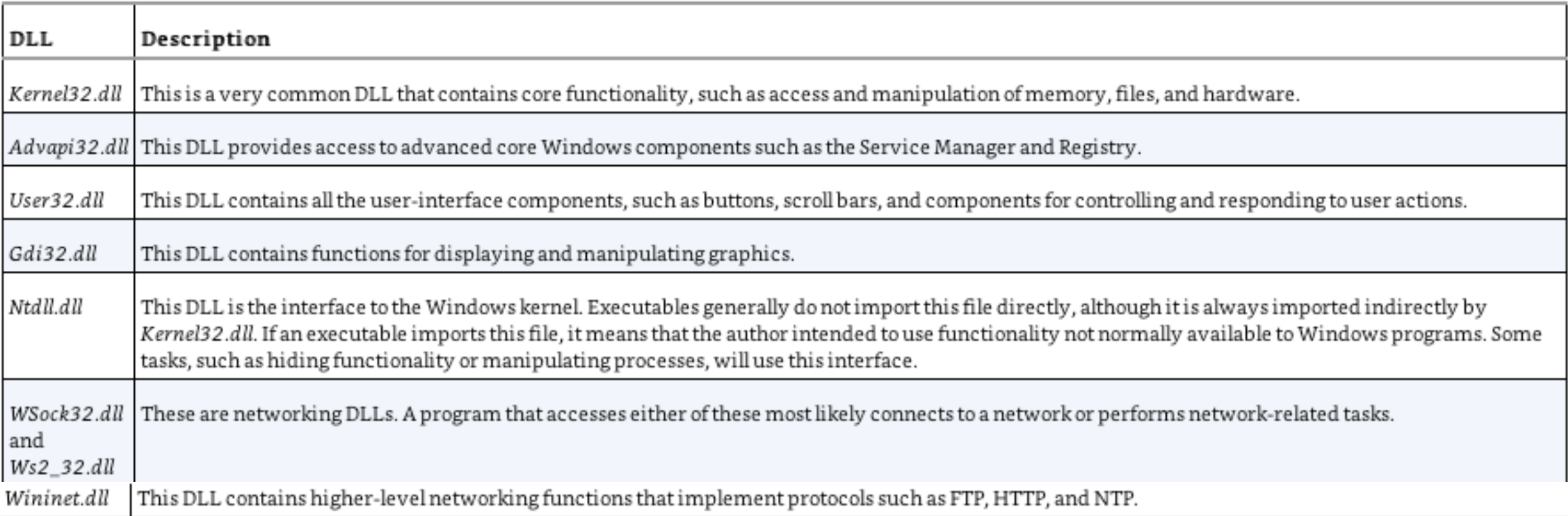
Examples of Imported functions
- OpenProcess, GetCurrentProcess, and GetProcessHeap
- open and manipulate processes
- ReadFile, CreateFile, and WriteFile
- FindFirstFile and FindNextFile
Strings
Simple tool – find all the strings that are accessible in the file
Resources
Resource Hacker
- View the sections inside the application
- View the resources that are associated with it
- Inspect any images, icons, dialogs and other resources inside
Advanced Static Analysis
The only real tool for the job: IDA
Graph and Text Mode
- Spacebar switches mode
Functions
- Shows each function, length, and flags
- L = Library functions
- Sortable
- Large functions usually more important
Names Window
- Every address with a name
- Functions, named code, named data, strings
Imports & Exports
Structures
- All active data structures
- Hover to see yellow pop-up window
Function Call
- Parameters pushed onto stack
- CALL to start function
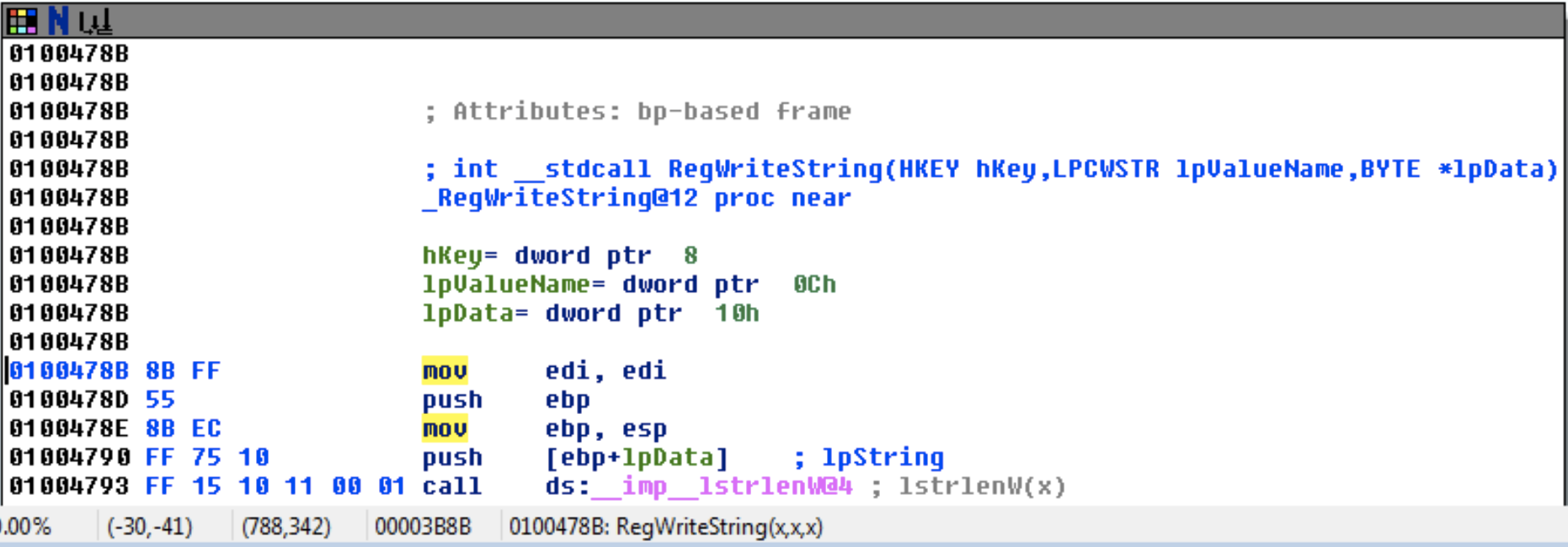
Jump to Location
- Press G
- Can jump to address or named location
Searching & Function and Argument Recognition
- IDA Pro identifies a function, names it, and also names the local variables
- It's not always correct
Advanced Analysis
- You are only looking to see if you can spot anything interesting, you’re not trying to reverse engineer the whole thing
- Look up strings and function calls and see if there is any interesting code around it
- For UPX packed binaries, you’ll need to unpack them first
- Don’t worry about reverse engineering other packed binaries!